Password managers are not the same
Use any password manager you want to, but it's better to choose wisely
Malicious actors frequently steal data from various companies, services, and even government agencies. A portion of these actors are known through reported data leaks in the news and legally mandated notification rules, such as the FTC’s Data Breach Response: A Guide for Business.
Although individuals should believe that companies make sufficient efforts to protect their data, errors can still occur. Even with companies’ best efforts, malicious actors can still access the protected layer. Either it’s a human error1, or lack of investment to security part of the company2, or targeted attack3, it affects the company and its customers.
There are numerous groups of individuals who are constantly working on exploring novel methods to exploit vulnerabilities in software and infrastructure to gain unauthorized access to data. Passwords (or any other authentication credentials, which we will discuss in more detail later in the article) serve various purposes, for example (these are just high-level examples, not an exhaustive list):
If a service’s database is stolen and authentication credentials are leaked, those credentials can be used to access accounts of those individuals in other services (for instance, if a service A is hacked, and a person uses the same credentials to access their B account).
If stolen auth credentials are obtained from a direct user’s device (for instance, a virus uploaded to a Windows PC), they can be used to access a target service, as well as other services the person used the same credentials for.
A simple login/password system can be brute-forced in certain cases (when an attacker knows the login credentials and attempts various passwords to gain access to the account).
There are more advanced methods to improve security, like physical devices, but in this article we will focus on password managers only.
Password managers
A password manager is a software application that securely stores authentication information for various services. By using a password manager, users only need to remember a single password, making it easier to manage their online accounts.
This solution eliminates the need to remember passwords for every website and even makes passwords in a “rememberable” format unnecessary. By using password managers, we can generate unique passwords within the password manager for each website or service and ensure they are as long and unique as possible.
By reviewing a list of the most common passwords4, we can see that they include those patterns:
Sequence of symbols from the qwerty5 keyboard
Combination of words
Repeated symbols
Combinations of them
And more complicated patterns, but they are still quite predictable
However, this list is expected to be this way because people are forced to remember passwords. In case a password manager requires a unique single password, people can create more complex passwords to remember, but it’s much different for many unique passwords.
Password managers help to keep passwords unique for every service you use.
Since we identified the positive part for password manager in managing passwords (that obvious from the name), those software applications provide more cool features, like:
Storing passkeys6
Storing 2FA7 secret key for code generation
Storing an additional notes or/and other fields (like answers to secret questions, etc)
To enhance the security of your accounts, utilize all available advanced authentication methods, such as password-less or two-factor authentication.
Alright, if password managers are so effective, how do they ensure the security of all our passwords?
Not the same
Password managers are not all the same! While it doesn’t mean we shouldn’t use them, I would argue that most password managers are superior to using them than don’t. It’s wonderful that we live in a world with competition, as we now have options.
I’d prefer to keep it simple and avoid going into details. However, if you’re interested in learning more about the security aspects of the discussed options, feel free to let me know. I have plans to write about it in more detail.
Meanwhile, many products offer integrated options, while standalone solutions are also available. While we would like to assume that all options are secure and ready for use, we will prioritize enhancing security in depth. We will ensure that your chosen password manager becomes one of the most secure on the market!
Before we will move forward, we will need to highlight one new word encryption8. Encryption helps to hide information from other parties. There is one the most secure way is end-to-end encryption9, when only a user who encrypted data, can read it.
Without diving into too much details, there are two high-level options:
Encryption keys are managed by a company
End-to-end encrypted
In this article, we will assume that all password managers used by readers of this article utilize encryption and avoid storing plain data. They adhere to all the best security practices, even when key management is handled by a company.
Encryption keys managed by a company
It’s a challenging aspect. There’s no absolute guarantee that proprietary software employs the most secure practices and provides the advertised level of security in its documentation or website.
When we can’t be certain about the encryption method, we can infer the high-level concept from a single indicator: restoring access to our passwords.
Our primary objective is to ensure the best security of our passwords (authentication information). This means we would prefer to restrict access to only ourselves. Even skilled hackers capable of stealing all information from our password managers’ company or governments requesting access to our data should not gain access to our passwords.
Based on this expectation, we shouldn’t have the ability to restore access without using our own secrets. If our password manager can restore access using our email, SMS, phone, or private information, someone else could gain access to all our passwords and other information.
If the password manager can be restored using any process other than providing our secrets, it means that malicious actors can also access it.
Those ways of restoration are not possible with end-to-end encryption.
End-to-end encrypted
In a very simple case, our password is required to access an end-to-end encrypted data (in our case, our password manager). It has a negative side, we loose an access to all our passwords by loosing our master password10.
There are pros and cons there:
Pros:
All the data is end-to-end encrypted
No one can get an access to our passwords
Our passwords are protected by our own level of security (our password)
Cons:
If we loose our password, we loose an access to all our passwords
Our passwords are protected by our own level of security (our password)
It’s quite secure and make sense to finish the article:
end-to-end
we control a level of security
But since we identified that people are not really good in creating passwords and remembering them. So, maybe there is an option how to make it more secure by adding a level of security to our password?
End-to-end encryption based on password and secret key
What if we will have two levels of security? Let’s assume we have two passwords instead of one:
Very long and randomly generated secret key/recovery key to encrypt data
Rememberable password we use to unlock our passwords
Let’s see a simple graph on how secret key is better than our the best passwords:
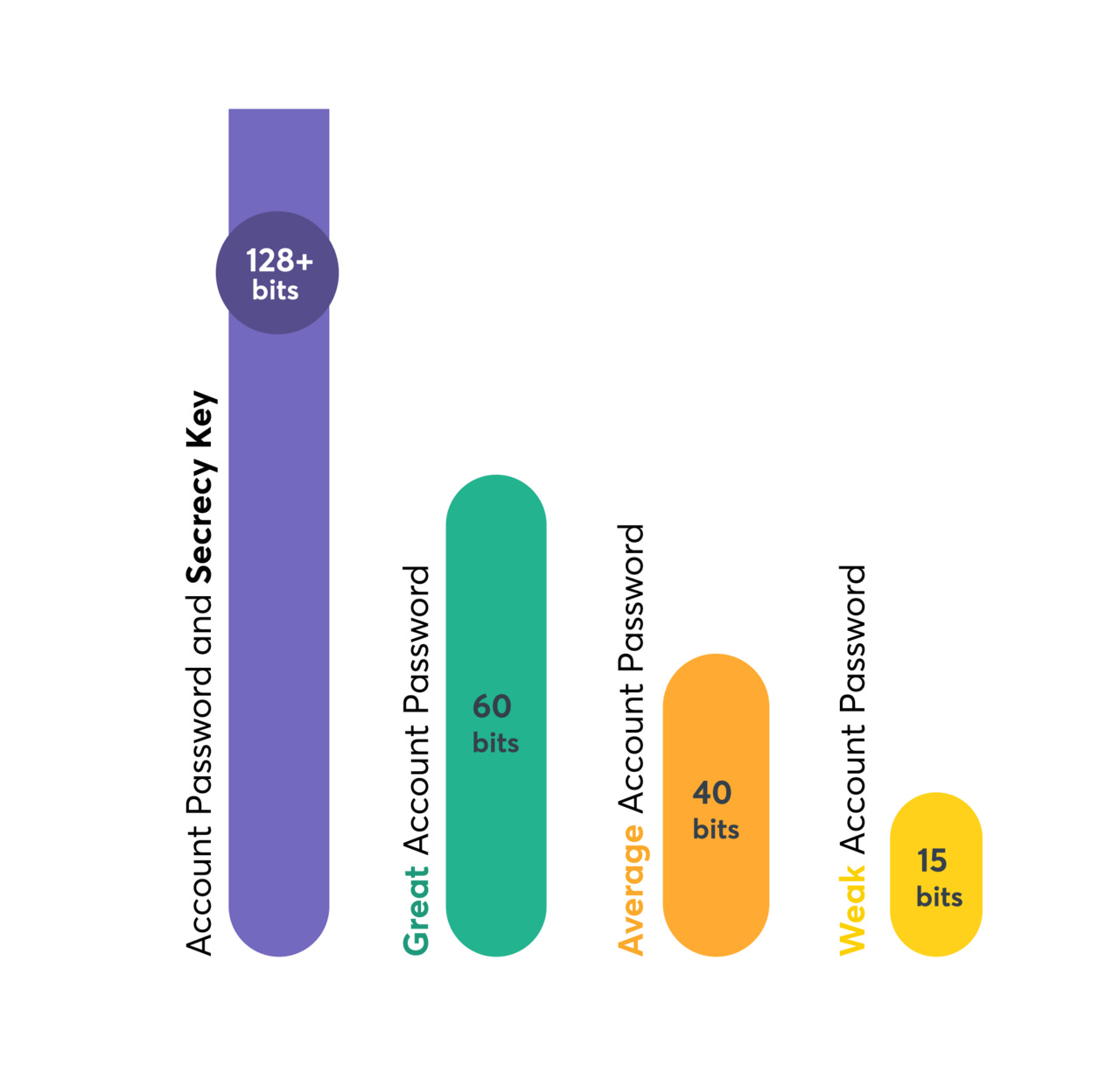
As we can observe from the image, the secret key can, most likely, will be significantly more secure than regular passwords.
This implies that two things must be compromised by malicious actors: our security key and our password, even though we should only use the secret key once when we begin using the password manager.
Disclaimer: The password managers I’ll mention in this article aren’t necessarily the most objectively best or most secure options. Nevertheless, I’m aware of these services and believe they provide effective solutions to safeguard our passwords.
This approach isn’t exclusive and can be found in various solutions. It’s quite similar to two-factor authentication (2FA) when we need to input the second factor to sign in to an account.
Final thought
If you haven’t started using a password manager yet, now is the best time to do so. You have a better understanding of password managers and how to select options with the best security.
Always remember to check the credibility and reputation of the solution. Usually, if a password manager is compromised, there will be news about it. Simply search the internet, and in general, it should be sufficient for most cases.
Once you’ve identified credible solutions, it’s time to assess their security level. If a chosen password manager mentions end-to-end encryption, it’s already a good sign. However, it makes sense to delve deeper and determine if there’s a way to restore your passwords without recovery keys. Ideally, it shouldn’t have a way to restore access.
In cases of good enough security, there are often additional security measures, such as secret keys or recovery keys. Only passwords may not provide sufficient security.
And finally, I believe one of the most important aspects is what I would suggest. I prefer not to make any advertisements, but I’ve decided to highlight two options that I genuinely believe provide good security levels (on March 2025):
The ultimate solution is 1Password. It offers a secret key and multi-platform clients with unique and specific recovery keys (that can be stored in a safe). Additionally, it’s a good solution because it supports multiple custom fields per stored password and encrypted files.
Apple’s Passwords, but only with enabled Advanced Data Protection for iCloud. Ensure that Advanced Data Protection is not disabled in your region, as it was disabled in the UK. Outside of that, this is a secure feature, considering some countries require it to be disabled.
Always conduct your own research and ensure that the solution you find is secure enough to proceed with it. Good luck on your more secure journey through the internet!
The most popular human error could be related to phishing attacks and other types of social engineering, but it’s also could be a skill-based errors and decision-based errors during product development and support.
Security is costly. Often, it involves a trade-off between the cost of developing products with simplified processes for teams and the quality of security.
Security cannot be absolute, it’s always a tradeoff. The task for every organization and individual to make an attack less valuable than cost of an attack.
QWERTY layout was devised and created in the early 1870s by Christopher Latham Sholes, a newspaper editor and printer who lived in Kenosha, Wisconsin, see details in Wikipedia.
Multi-factor authentication is security feature, when after correct password the second verification step will be requested. It could be a unique code sent to email, or sms, or ask to fill a randomly generated code TOTP (time-based one-time password).
In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode.
End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages.
Master password is a password that is used to restore an access to our data. This password is not stored anywhere and no one can get an access there, except of the owner of the password.


